Diabolical DNSSEC
In my previous post, we identified issues related to DNSSEC.
Google’s documentation explains it well here. Essentially it authenticates responses to domain name lookups so that these responses cannot be spoofed by other servers.
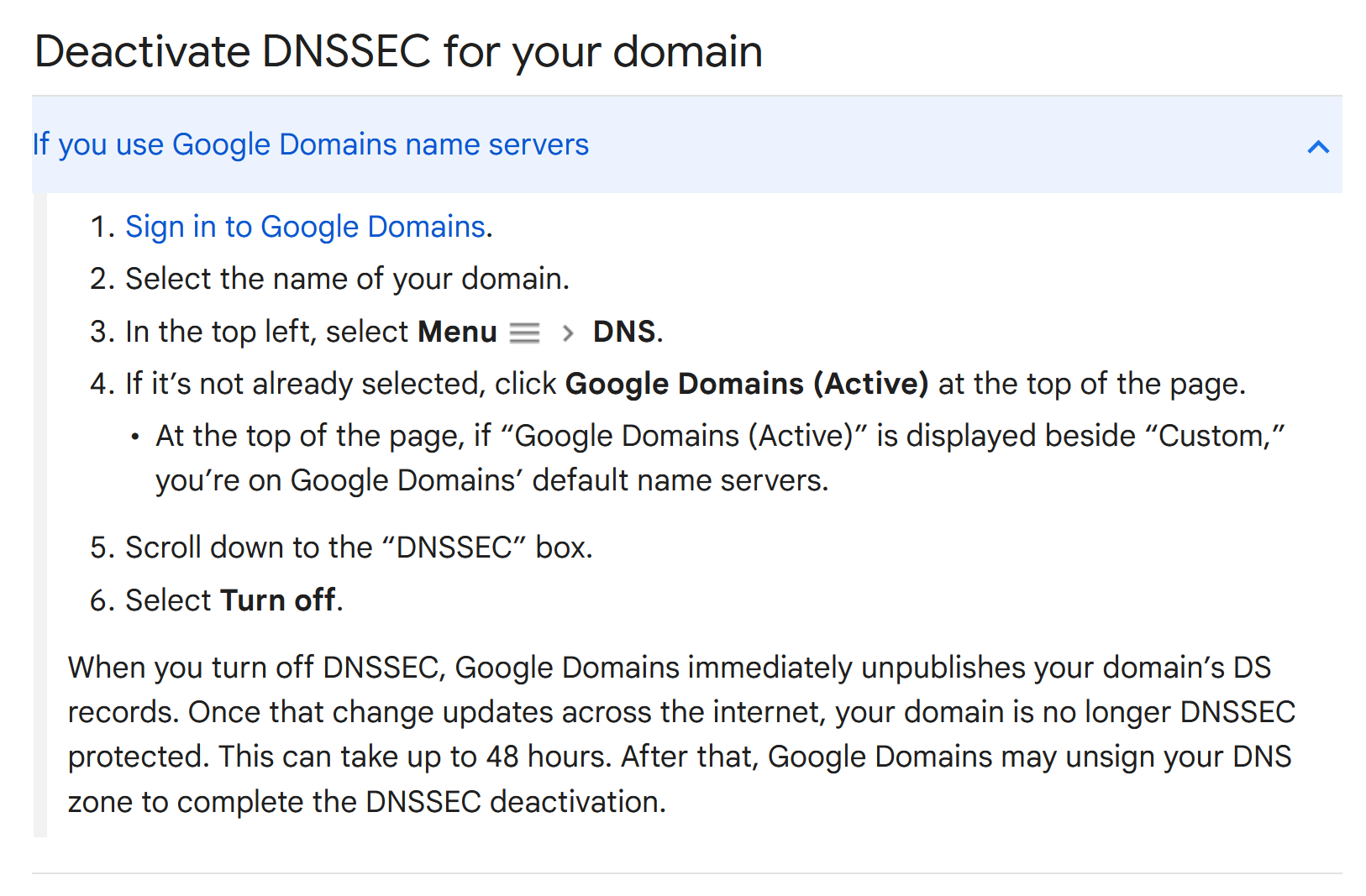
Because its a hassle to configure and use, i’ve decided to do away with it. However, I have found out how I can identify if my DNS is still configured with DNSSEC. It takes roughly 24 hours for configurations to propagate in GCP, so this helps me get an idea of when its ready.
The easiest way would be to use the dig tool. We should be able to identify the presence of DNSSEC by looking at the DS parameter. This guide provides more details.
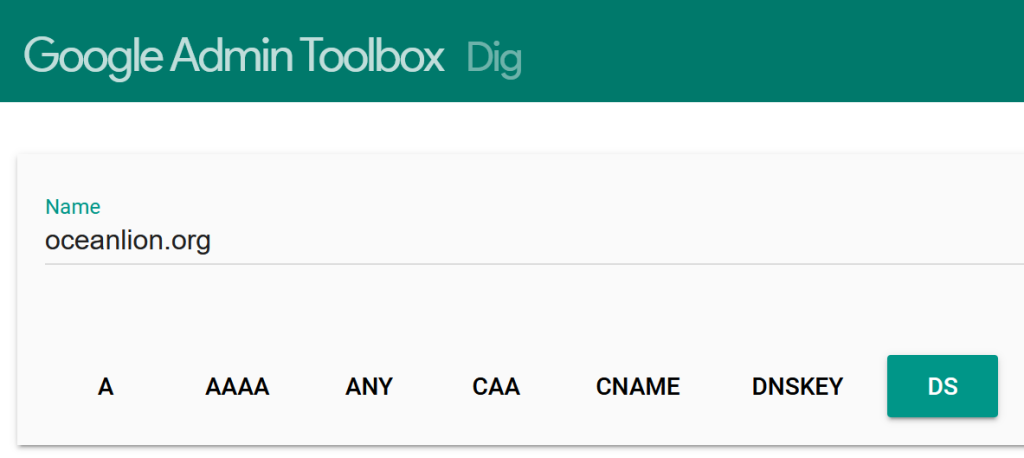
Not immediately intuitive, but I imagine an experienced professional would’ve been able to resolve this in a heartbeat. Now I’ll have to wait for my configurations to propagate.